Cloudflare DDoS Protection
Cloudflare provides a robust layer of DDoS protection for your server and applications.
When using Cloudflare’s Proxy, CDN, and security features, all incoming traffic to your Coolify-hosted apps is shielded from malicious attacks, like DDoS, and secured through Cloudflare’s global network.
Why Use Cloudflare for DDoS Protection with Coolify?
- Blocks malicious traffic before it reaches your server, reducing risk and server load.
- No need to scale server resources during DDoS attacks — Cloudflare absorbs the impact.
- Minimal configuration required to enable robust protection against potentially costly attacks.
- Hides your server’s real IP address by resolving your domain to Cloudflare’s IPs.
When Not to Use Cloudflare for DDoS Protection
- You prefer not to route all traffic through Cloudflare’s network.
- Privacy concerns, Cloudflare terminates TLS, which means they can inspect incoming requests.
- Cloudflare downtime, although extremely rare, could affect your service if you rely entirely on their protection.
- You want full control over SSL/TLS certificates issued by a global Certificate Authority.
- You need free wildcard support for deep subdomains (more than 1 level subdomains -- e.g.,
*.sub.domain.comwhich Cloudflare does not offer for free).
The following data is used as an example in this guide. Please replace it with your actual data when following the steps:
- IPv4 Address of Origin Server: 203.0.113.1
- Domain Name: shadowarcanist.com
- Username: shadowarcanist
1. Create the Origin Certificate
Communication between your server and Cloudflare is encrypted using a custom Cloudflare Origin Certificate (required when using Cloudflare’s proxy).
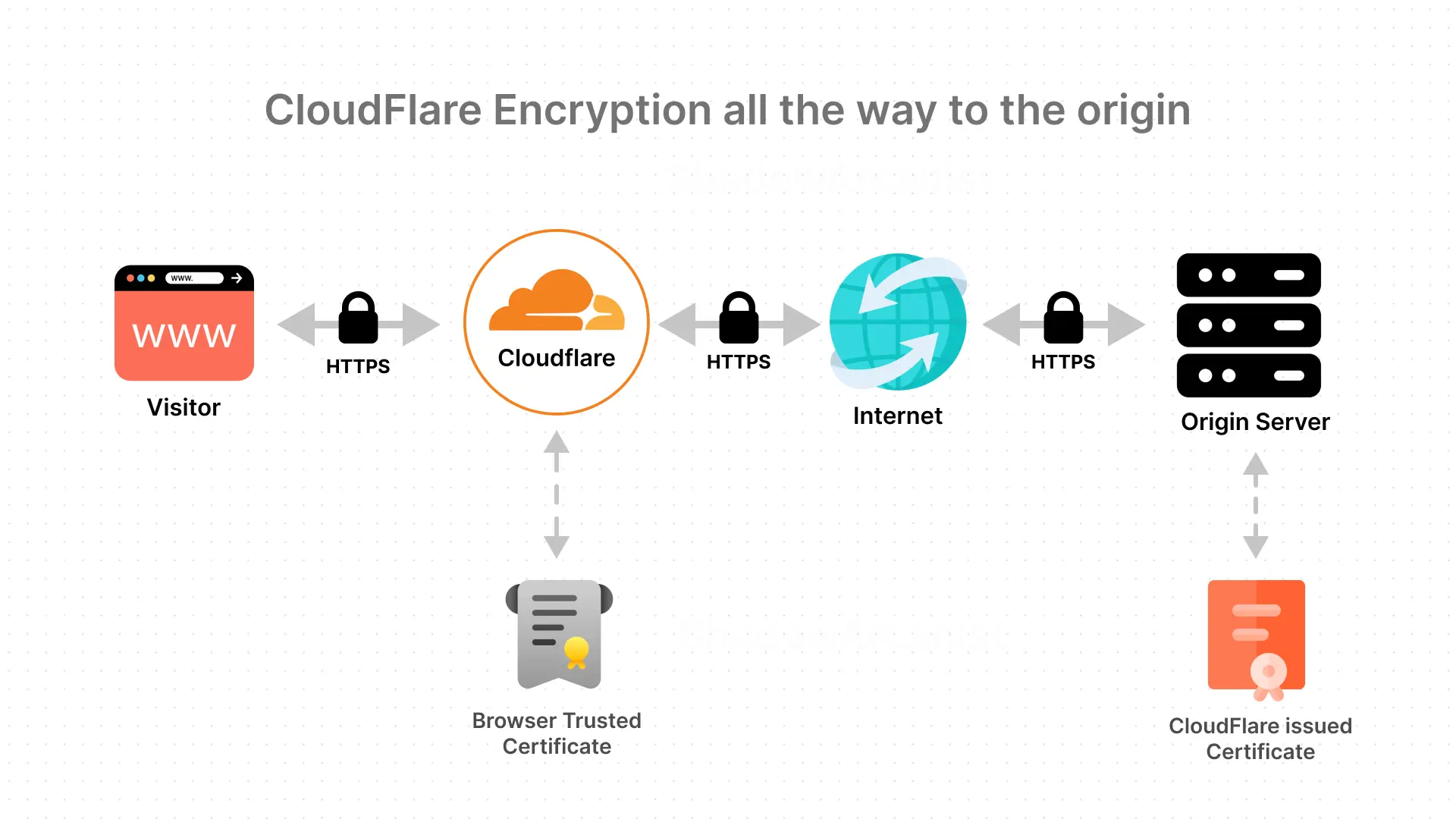
To create your Cloudflare Origin Certificate, follow these steps:
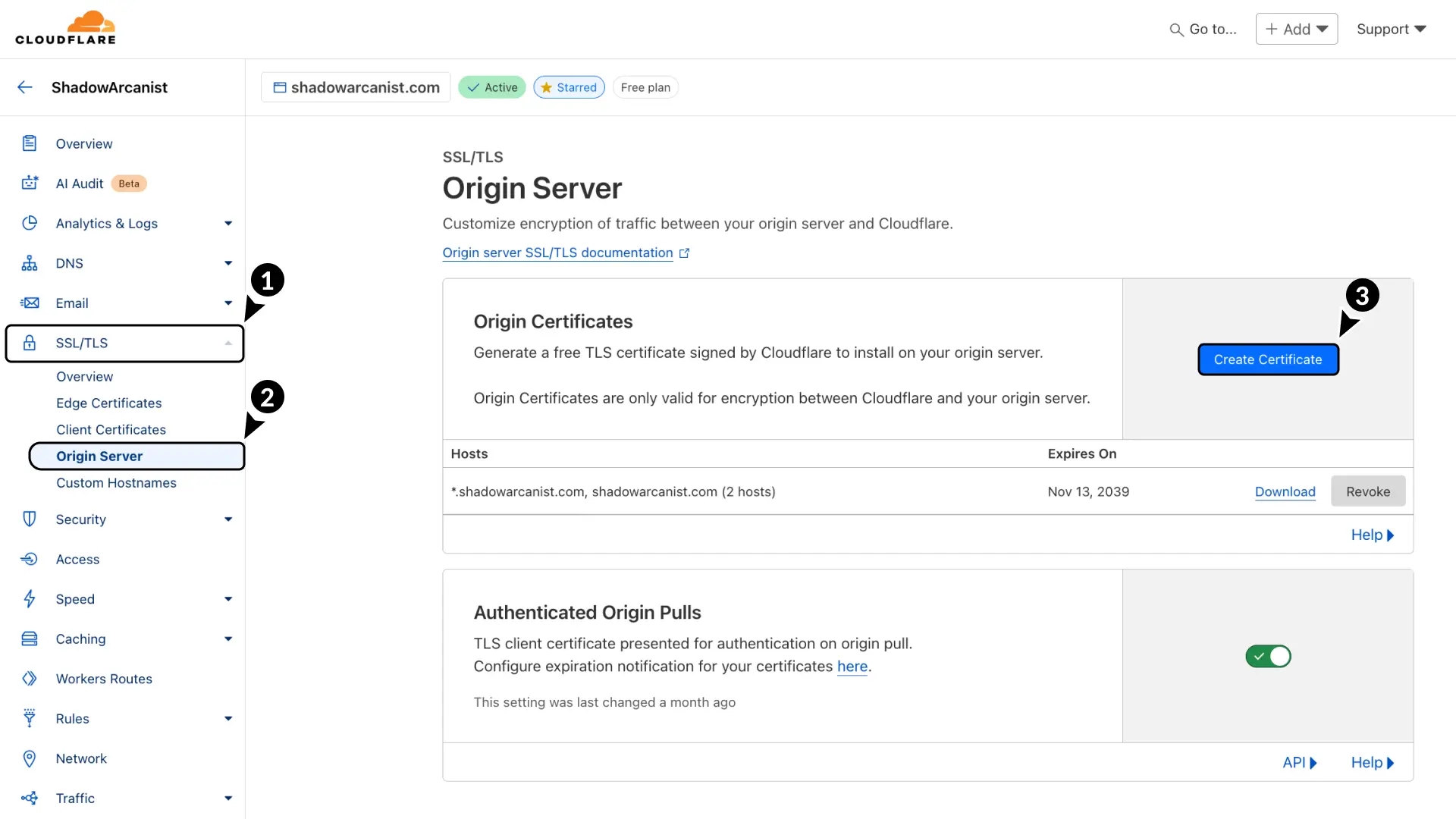
- In your Cloudflare dashboard, go to SSL/TLS.
- Select Origin Server.
- Click the Create Certificate button.
You’ll be asked to choose a private key type, hostnames, and certificate validity.
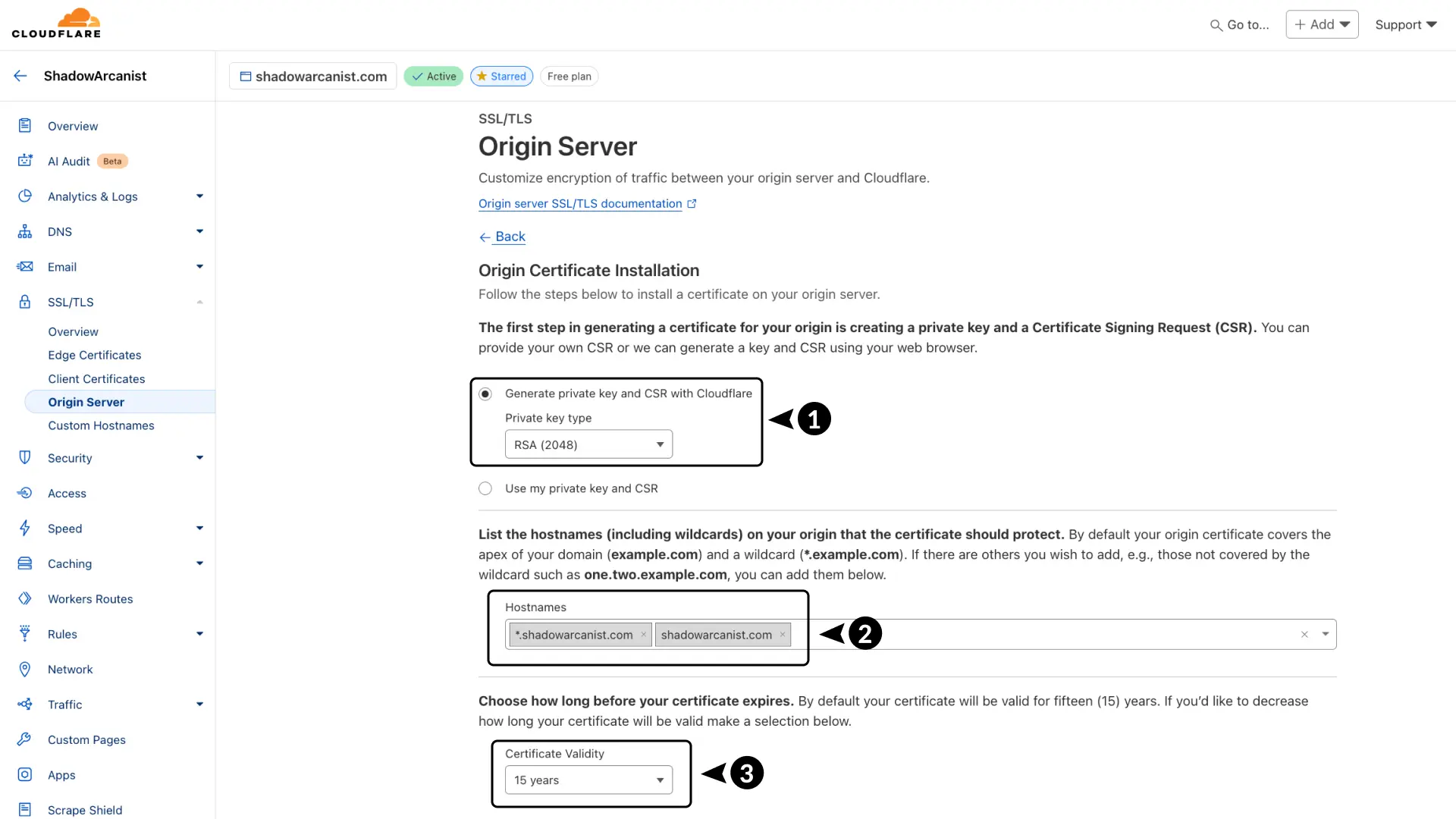
- Choose RSA (2048) for the key type.
- Add the hostnames you want the certificate to cover.
shadowarcanist.comwill cover only the main domain.*.shadowarcanist.comwill cover all subdomains.
On Cloudflare’s free plan, wildcard certificates cover just one level of subdomains
For example, it works for coolify.shadowarcanist.com but not www.coolify.shadowarcanist.com.
To cover multiple levels, you'll need to purchase the Advanced Certificate Manager ↗
- Set the certificate validity to 15 years.
Your certificate will now be generated.
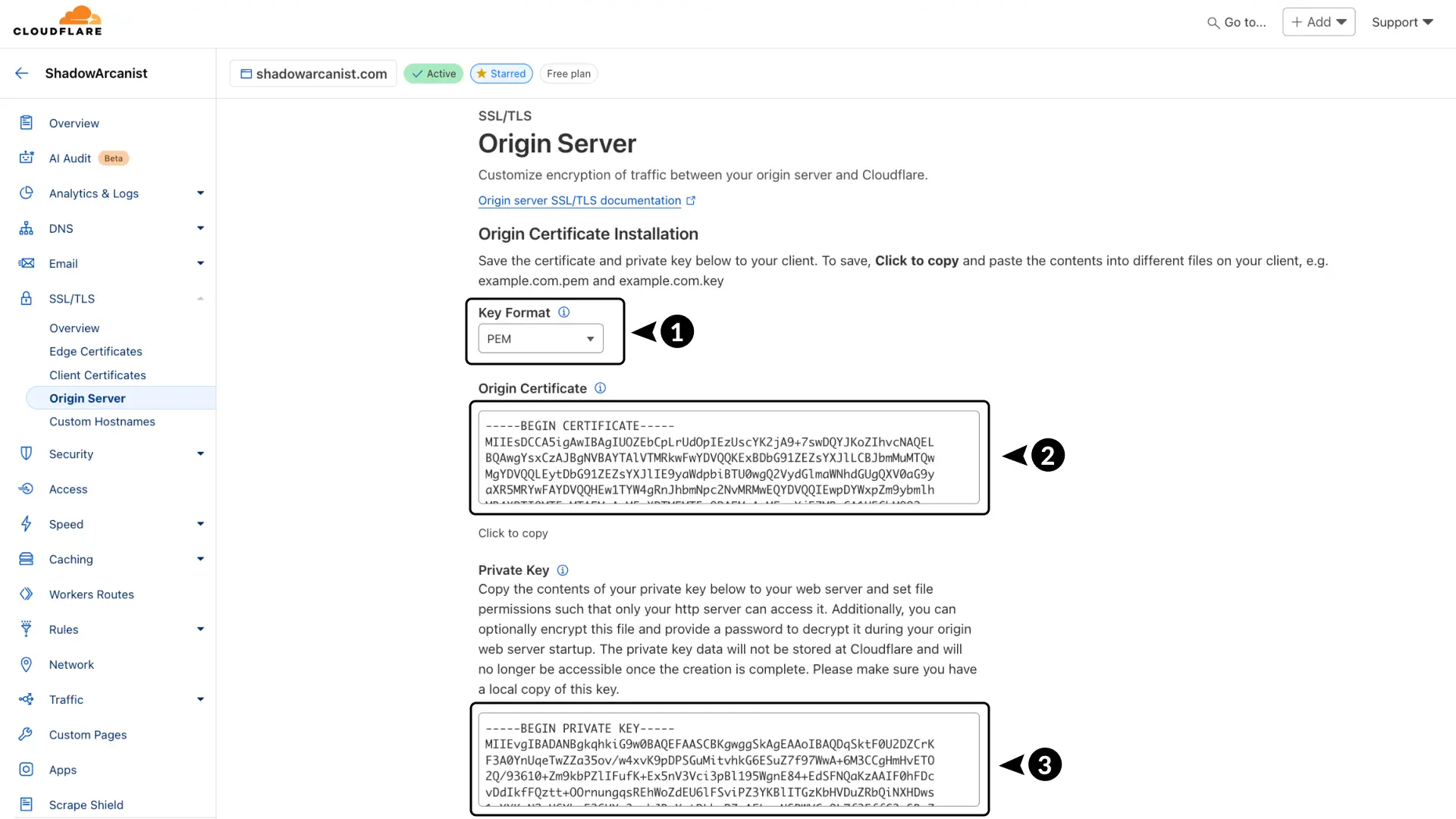
- Choose PEM as the key format.
- Copy your Certificate.
- Copy your Private Key.
Next, you'll add these to your server running Coolify and configure Coolify to use this certificate.
2. Add Certificate to Your Server
SSH into your server or use Coolify's terminal feature. For this guide, I’m using SSH:
ssh [email protected]Once logged in, navigate to the Coolify proxy directory:
$ cd /data/coolify/proxyAdding certificates slightly varies for Caddy and Traefik proxy so choose the correct one from the below section
Create the certs directory:
$ mkdir certsVerify it was created:
$ ls
> acme.json certs docker-compose.yml dynamicNow, navigate into the certs directory:
$ cd certsCreate two new files for the certificate and private key:
$ touch shadowarcanist.cert shadowarcanist.keyVerify the files were created:
$ ls
> shadowarcanist.cert shadowarcanist.keyOpen the shadowarcanist.cert file and paste the certificate from the Cloudflare dashboard:
$ nano shadowarcanist.certSave and exit after pasting the certificate.
Do the same for the shadowarcanist.key file and paste the private key:
$ nano shadowarcanist.keySave and exit.
Now the origin certificate is installed on your server.
3. Set Up DNS Records and TLS Encryption
To make the origin certificate work, configure your DNS records, enable TLS, and set up HTTP to HTTPS redirects in Cloudflare:
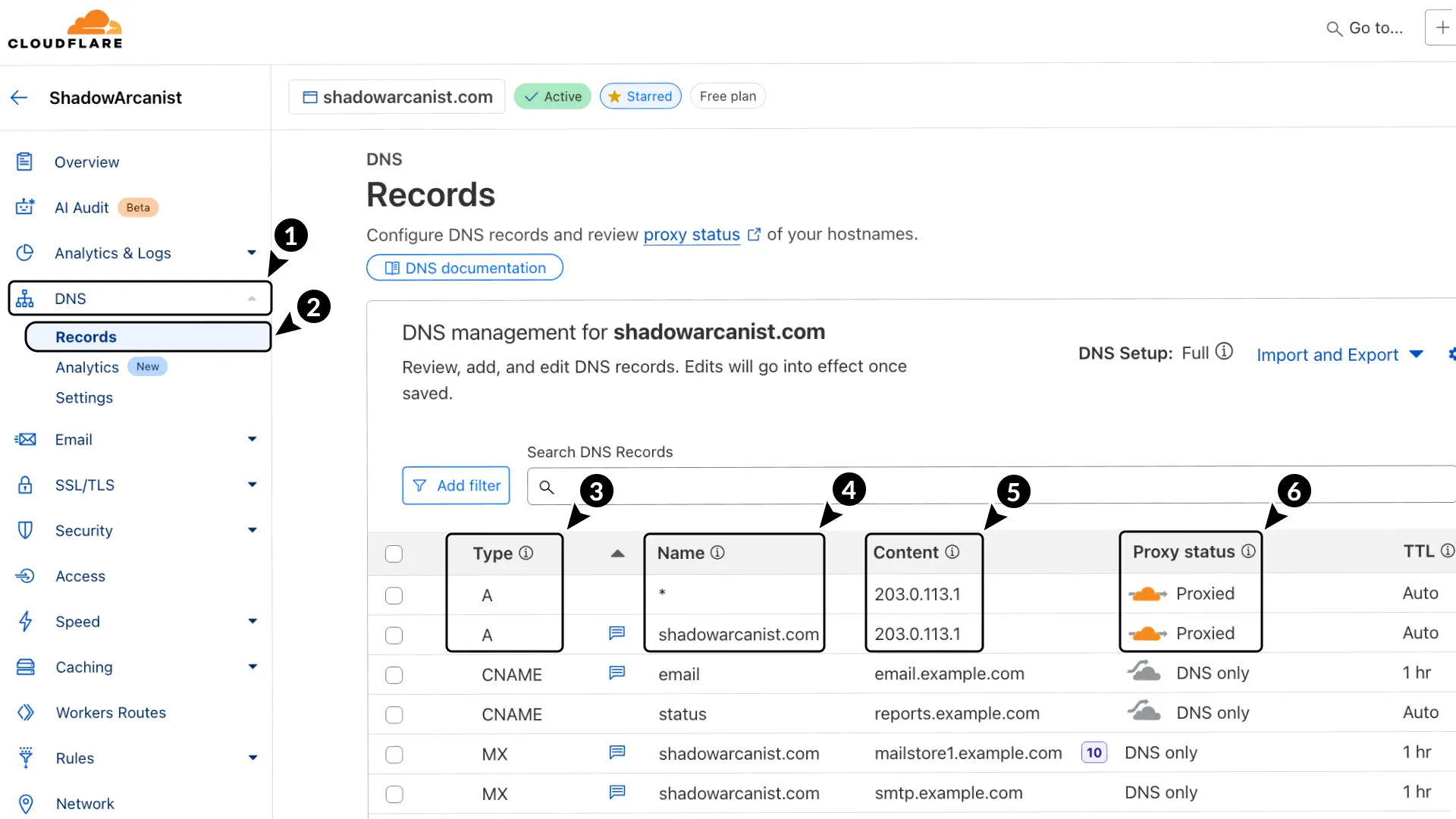
- In Cloudflare, go to DNS.
- Select Records.
- Add 2 A records:
- Enter name as
shadowarcanist.comand* - Use the IP address of your server as the content for both records.
- Set the proxy status to Proxied for both records.
Enabling the "Proxied" (orange cloud) option for both A records — shadowarcanist.com and * — will proxy the root domain and all one-level subdomains via a wildcard.
This isn't necessary if you only need to proxy (or protect against DDoS) for a specific domain. In that case, simply enable proxying for the domain you want protection for.
Next, set up TLS encryption:
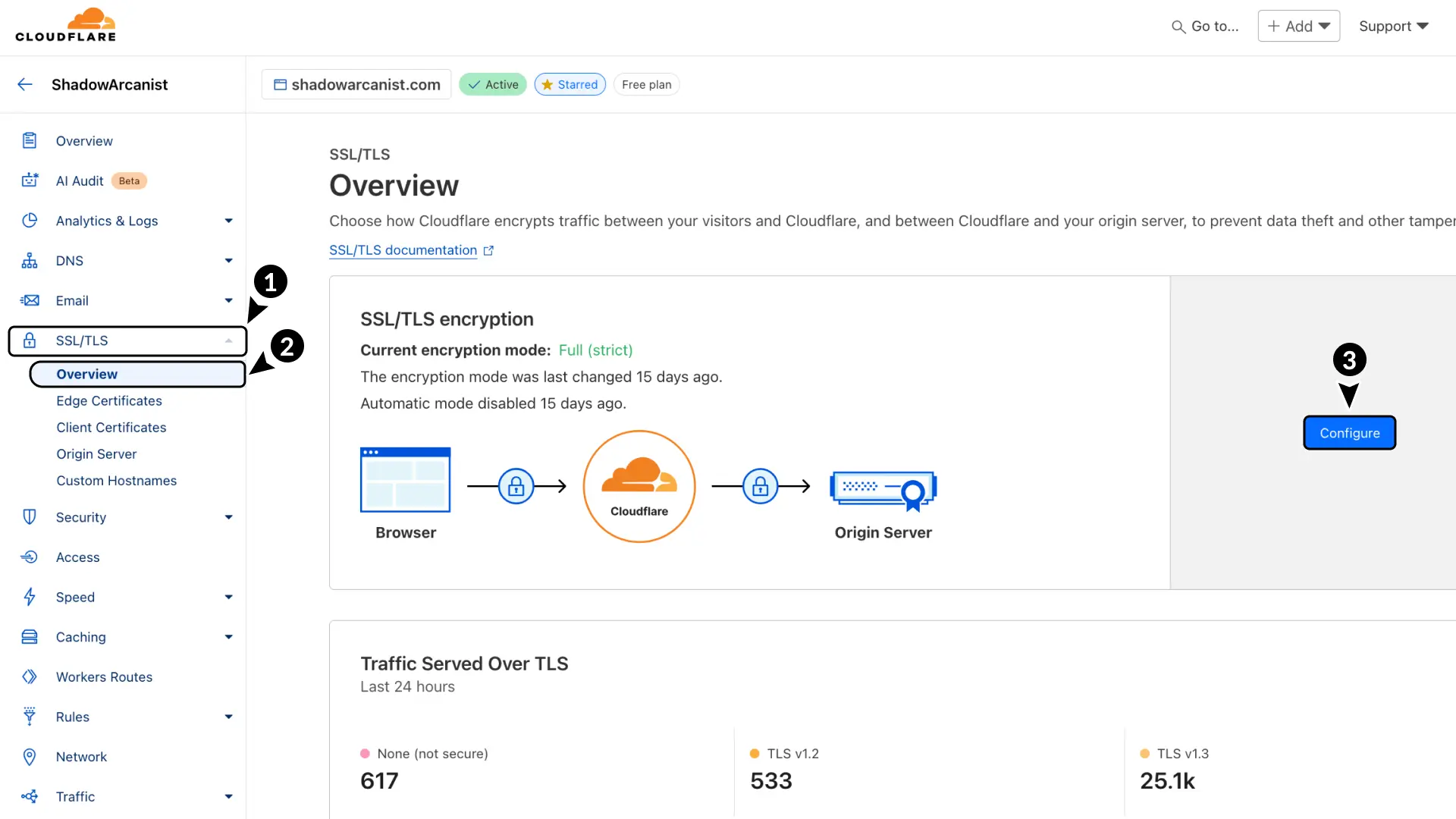
- Go to SSL/TLS in Cloudflare.
- Select Overview.
- Click Configure button
Choose Full (Strict) as the encryption mode.
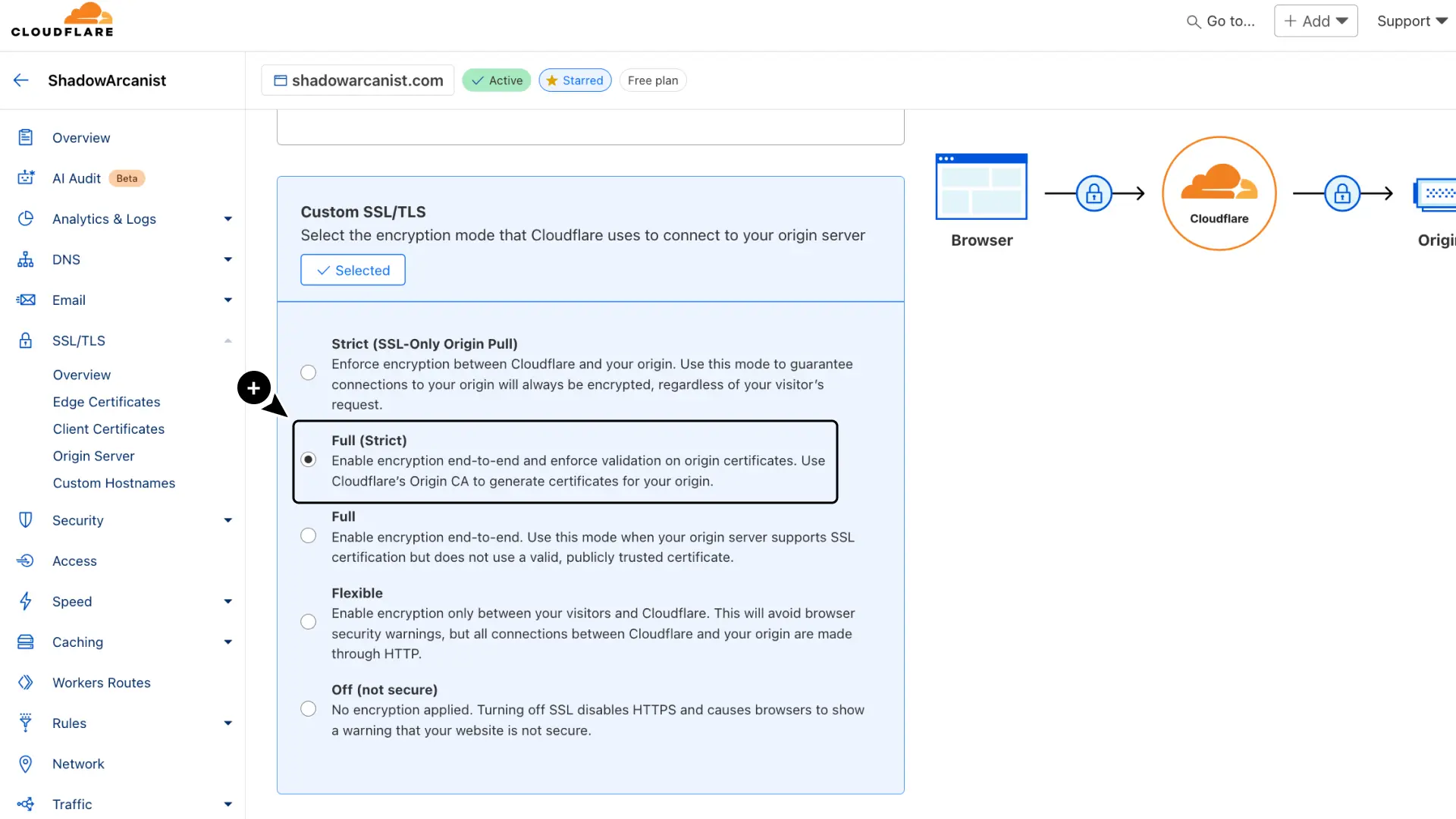
Finally, enable HTTP to HTTPS redirects:
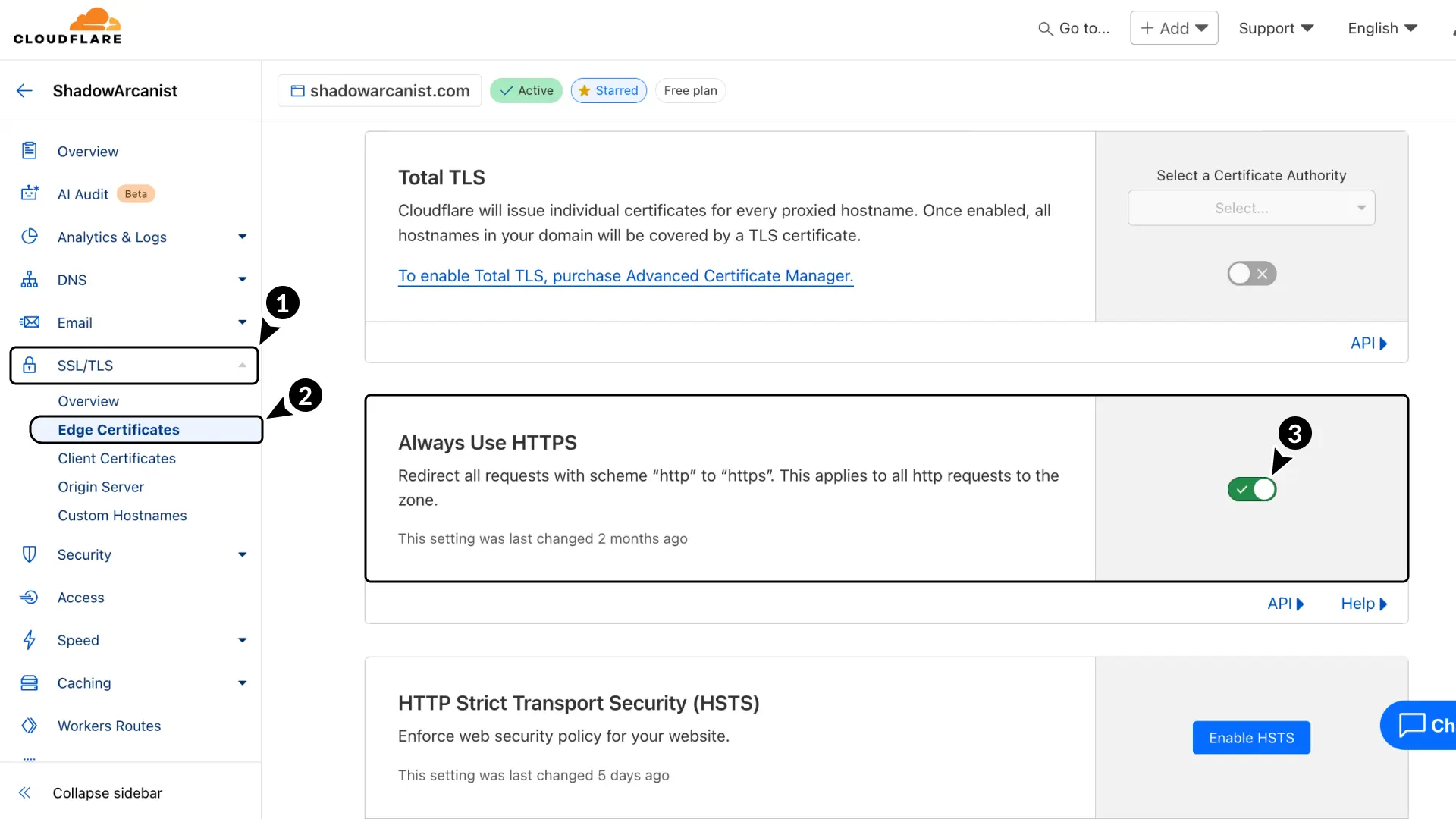
- In Cloudflare, go to SSL/TLS
- Select Edge Certificates.
- Enable Always Use HTTPS.
4. Configure Coolify proxy to Use the Origin Certificate
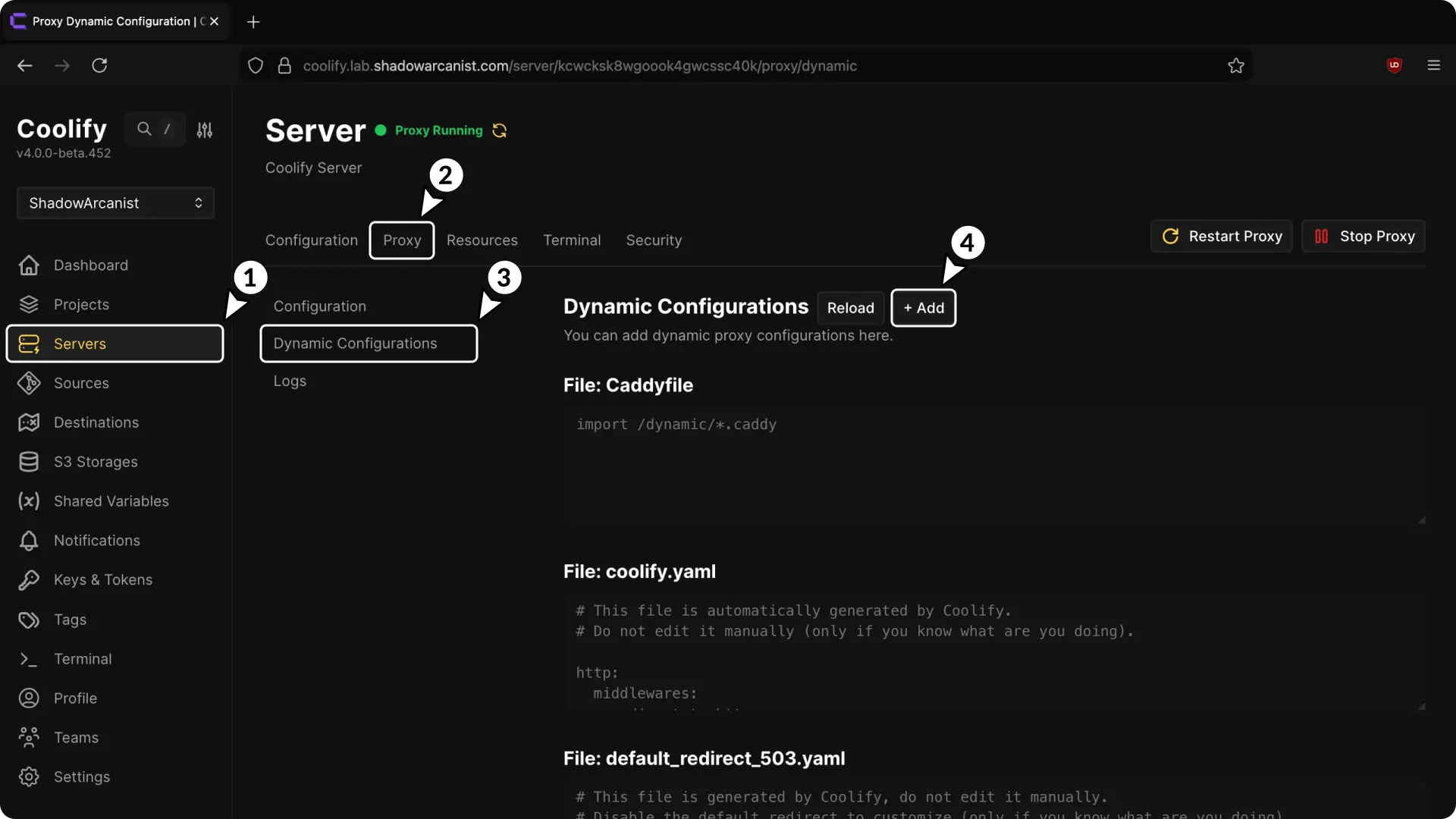
- Go to the Server section in the sidebar.
- Select Proxy.
- Open the Dynamic Configuration page
- Click Add button
You will now be prompted to enter the Dynamic Configuration.
Adding Dynamic Configuration slightly varies for Caddy and Traefik proxy so choose the correct one from the below section
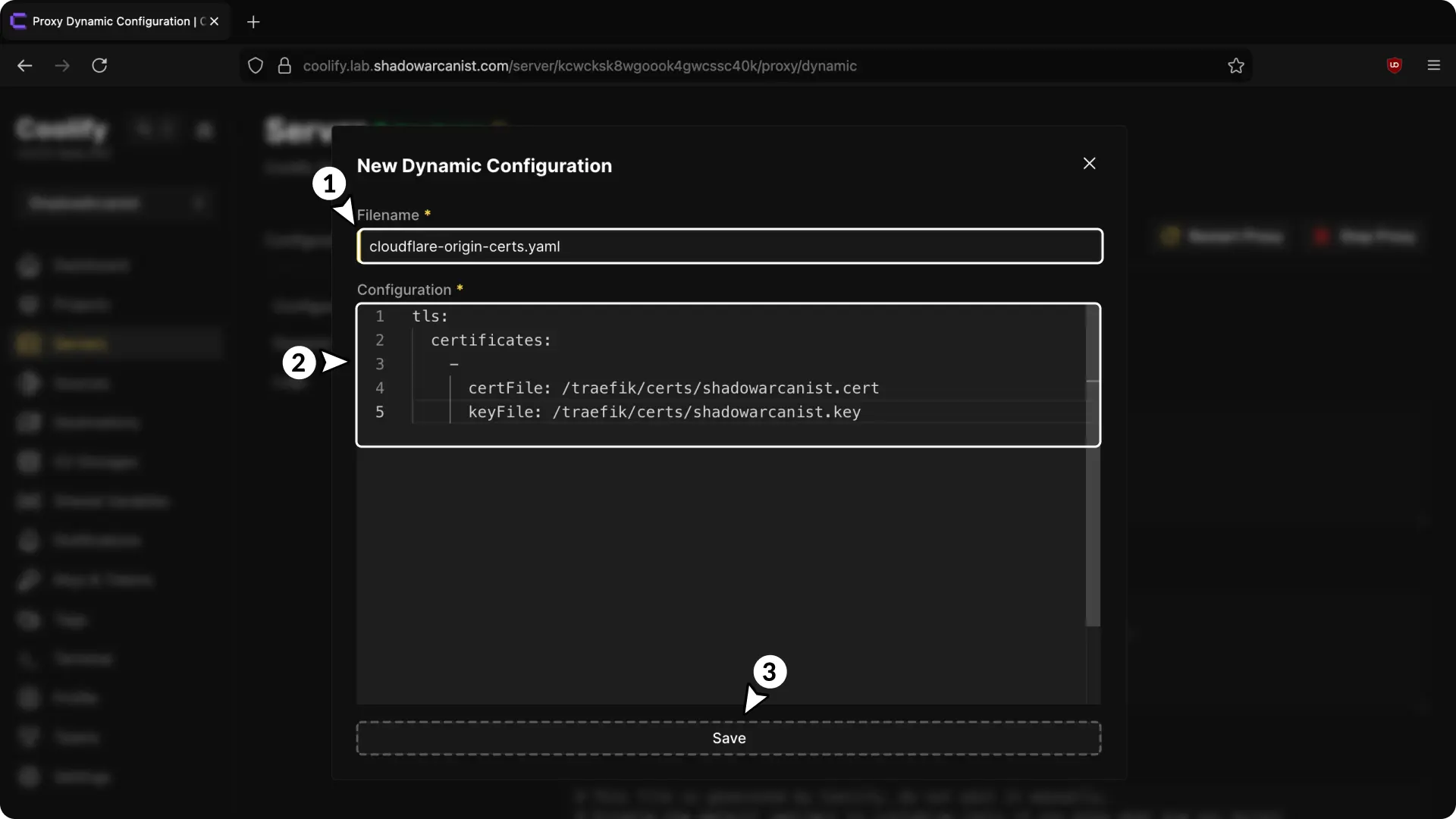
- Choose a name for your configuration (must end with
.yaml). - Enter the following details in the configuration field:
tls:
certificates:
-
certFile: /traefik/certs/shadowarcanist.cert
keyFile: /traefik/certs/shadowarcanist.key- Save the configuration
If you want to add multiple certificates and keys, you can do it like this:
tls:
certificates:
-
certFile: /traefik/certs/shadowarcanist.cert
keyFile: /traefik/certs/shadowarcanist.key
-
certFile: /traefik/certs/name2.cert
keyFile: /traefik/certs/name2.key
-
certFile: /traefik/certs/name3.cert
keyFile: /traefik/certs/name3.keyFrom now on, Coolify will use the origin certificate for requests matching the hostname.
Now you’re done! Your server is set up to use the Cloudflare Origin Certificate, and all traffic is proxied through Cloudflare network so all incoming attacks like DDoS are prevented by Cloudflare before it reaches your server.
All the steps below are optional. Cloudflare should already be protecting your applications. Follow the below steps if you want to prevent attackers from directly attacking your server by it's IP Address on Port 80 and 443
5. Configure Firewall to Allow Only Cloudflare Traffic
Configure your firewall to allow incoming traffic on port 443 only from Cloudflare’s IP ranges ↗.
Block all other inbound traffic, except for your SSH port.
This prevents attackers from bypassing Cloudflare and directly targeting your server with traffic on ports 80 or 443.
This step is completely optional but recommended.
Credits
The origin-cert-illustration image is designed using icons from Flaticon ↗. Links to each icon can be found below: